Cyber Resilience Importance For Organizations
Cybercrimes are becoming increasingly complicated and common in today’s technologically advanced environment. Cyber attacks constantly threaten enterprises, disrupting operations, compromising sensitive data, and undermining trust. The security of the company’s crucial business processes has to be its top concern if the organization wants to remain competitive in such a volatile market. However, today’s organizations can no longer rely just on cybersecurity measures to ensure their survival and success. This is where the concept of “cyber resilience” manifests as a crucial and vital strategy. A robust cybersecurity resilience strategy enables the organization to maintain business continuity before, during, and after a cybersecurity incident.
The term “cyber resilience” describes a business’s ability to foresee, address, and recover from cyber incidents while continuing to do business and reducing the effect of interruptions.
What is Cyber Resilience?
The term “cyber resilience” describes a business’s ability to foresee, address, and recover from cyber incidents while continuing to do business and reducing the effect of interruptions. A cyber-resilient organization can adapt to crises, risks, adversities, and known and unforeseen difficulties. Cyber resilience emphasizes a comprehensive and proactive strategy for addressing threats beyond conventional cybersecurity procedures. It comprises not just technological elements but also people, processes, and communication techniques.
Importance of Cyber Resilience
Business Continuity
Cyber resilience reduces cyber attacks by removing threats before they cause any harm. It guarantees that crucial business processes keep functioning both during and after cyber events. This minimizes the effects of interruptions during and after a crisis and cuts down on downtime. Additionally, as Cyber resilience reduces the downtime and intensity of cyber disasters, organizations can reduce the financial losses associated with data breaches, system outages, and recovery attempts. It aids businesses in adhering to regulations to prevent fines and other legal repercussions.
Improves Reputation
A data breach incident can damage a brand’s reputation and undermine consumer confidence. Therefore, having strong resilience contributes to overall data security efforts by helping to secure sensitive data from unauthorized access, theft, and adaptation. Additionally, it indicates the company’s dedication to customer satisfaction and data security. Some businesses also adhere to international standards, such as ISO 27001 from the International Organization for Standardization. ISO 27001 provides a solid foundation for building cyber resilience. It aids businesses in developing a more solid and flexible strategy for controlling cyber risks and disruptions.
Effective Incident Response
An organized incident response strategy is a crucial part of cyber resilience. This makes it possible for enterprises to react to cyber disasters swiftly and effectively, hence reducing their impact. Cyber resilience techniques strongly emphasize continuous monitoring and cyber incident learning. This proactive strategy enables businesses to respond effectively to new and emerging cyber threats. Organizations that invest in cyber resilience develop a security-conscious culture and are better equipped to tackle forthcoming challenges.
Competitive Advantage
Organizations may gain a competitive edge by demonstrating a strong cyber resilience plan, ensuring customers, partners, and investors of their dedication to safeguarding critical data. It can encourage an organization to adopt new technologies and innovations since it will be more prepared to handle any security issues that may arise. Organizations may set themselves up to face the difficulties of the digital age and emerge more resilient, flexible, and secure than before.
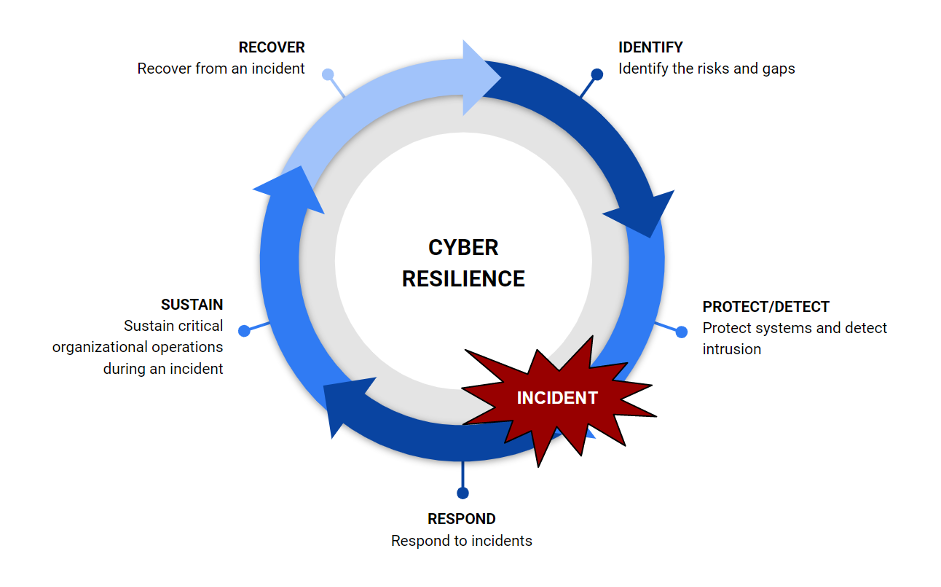
Key Components of a Cyber Resilience Framework
Identify
A cyber resilience program’s initial step is evaluating cybersecurity threats that might interrupt vital company functions and assets. This aids in managing and understanding the systemic risks to the business.
Protect
This stage entails deploying the required tools and technologies, putting security measures in place, empowering staff members through awareness and training, information security policies, identity management, and access control, as well as performing routine maintenance on the IT system.
Detect
This function specifies the necessary steps to recognize a cybersecurity occurrence and facilitate prompt detection. To safeguard systems from cyberattacks, system failures, and illegal access, entails ongoing monitoring to identify variations and cybersecurity concerns.
Respond
When a cybersecurity challenge happens, this function entails taking the proper action. This involves setting plans and measures in place to lessen the impact of unforeseen cybersecurity incidents, performing analysis to make sure an efficient response, and assisting recovery efforts.
Recover
This stage entails having the ability to quickly adapt, recover, and restore mission-critical systems in order to prevent business disruption. It guarantees that important business functions or capacities are not adversely affected. This process aids in the recovery of systems, applications, or data that a security breach or system failure has damaged.
Conclusion
Cyber resilience is about an organization’s capacity to endure and recover from risks. It is also about how organizations adapt, grow, and prosper in the face of adversity. Organizations may position themselves to withstand the difficulties of the digital era and emerge stronger, more flexible, and more secure than ever before by adopting cyber resilience. Candidates who want to learn more about cyber resilience can enroll in ISO 27001 Lead Implementer Training. Professionals may acquire new techniques for reducing cyber threats and disruptions with the help of training. They can anticipate, recognize, and take the appropriate security measures in response to adverse behaviors.
Source: https://unichrone.com/blog/isms/why-is-cyber-resilience-important-for-organizations/